Overview
 |
| Top to Bottom - Internet Explorer, Firefox, Safari, Chrome, and Opera |
Before going into Endpoint Security with Camel with EAP and Fuse, I wanted to provide a quick primer on Secure Sockets Layer (SSL). We will have a quick overview and then discuss 1-way and 2-way SSL. SSL should be the first step in protecting sensitive data across the network pipe. It will minimize the man-in-the-middle attacks and eavesdropping. SSL is the standard security technology for establishing an encrypted link between a web server and a browser. This makes sure the data passed between the server and browser or server and server remains private and not modified by providing encryption and trust.
Encryption uses a private key/public key pair which ensures that the data can be encrypted by one key but can only be decrypted by the other key pair. This is referred to as the Public-Key Infrastructure (PKI) Scheme. The public key is shared while the private key is kept locally. This is described more in 1 and 2 way SSL below concerning the files and which are stored where. This can also be extending to server to server communication, in addition to browser to server communication.
Trust is achieved through the use of certificate trust. Certificate trust can be thought of as a chain that starts with the Certificate Authority (or CA). A CA is a company or entity that issues SSL Certificates. Web browsers and systems come loaded with a list of recognized issuers and that list is kept up to date by automatic updates. Certificates can also be self-signed for testing.
Benefits of SSL through the CIA Triad
I blogged about the CIA Triad Model which is located here, The SANS institue has an excellent beginners guide to SSL and TLS which also describes the value of SSL/TLS in relation to the CIA Triad.
The C-I-A (Confidentiality, Integrity, Availability) Model for information security is addressed in several ways by the use of a secure communications protocol. Confidentiality of the information being passed is the main purpose of the SSL and TLS protocols. Integrity is addressed through the use of message authentication in each message from the first handshake. Additionally, non-repudiation is accounted for through certificate passing in addition to the integrity check from the message authentication. Though more responsibility for the Availability portion of the model (in this example) is placed on the server, Availability is slightly addressed since secure communications prevent malicious users from having direct access to the system.
Difference between SSL and TLS
Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are both cryptographic protocols designed to provide communications security over a computer network. The terms SSL and TLS are often used interchangeably or in conjunction with each other (TLS/SSL), but one is in fact the predecessor of the other — SSL 3.0 served as the basis for TLS 1.0 which, as a result, is sometimes referred to as SSL 3.1. In this document, the US Government describes TLS Guidelines for Implementation and indicates that SSL v3 not be used for sensitive government communications or for HIPAA-compliant communications. This chart does a good job with SSL/TLS support in browsers and the affected vulnerabilities (BEAST, POODLE, CRIME, RC4).
No SSL
Of course with no SSL data across the network is not encrypted. Using no SSL is usually done in a development or test environment.
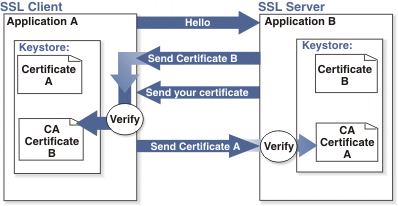
2-way SSL (Mutual or Client Authentication)
Two-way SSL authentication is also referred to as client or mutual authentication because the application acting as an SSL client presents its certificate to the SSL server after the SSL server authenticates itself to the SSL client.
- A client requests access to a protected resource.
- The server presents its certificate to the client.
- The client verifies the server’s certificate.
- If successful, the client sends its certificate to the server.
- The server verifies the client’s credentials.
- If successful, the server grants access to the protected resource requested by the client.
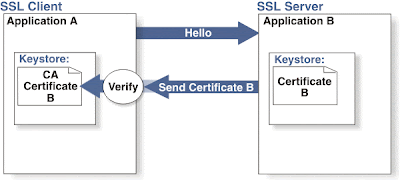
1-Way SSL
References:
http://www.sans.org/reading-room/whitepapers/protocols/ssl-tls-beginners-guide-1029
http://blog.vanillaforums.com/help/using-ssl-https-vanilla-forum/
http://en.wikipedia.org/wiki/Public_key_certificate
https://luxsci.com/blog/ssl-versus-tls-whats-the-difference.html
http://en.wikipedia.org/wiki/Transport_Layer_Security
https://luxsci.com/blog/ssl-versus-tls-whats-the-difference.html
http://mihalos.gr/2013/04/03/ssltls-protocol-overview-part1/
http://www.codeproject.com/Articles/326574/An-Introduction-to-Mutual-SSL-Authentication
https://luxsci.com/blog/ssl-versus-tls-whats-the-difference.html
http://en.wikipedia.org/wiki/Transport_Layer_Security
https://luxsci.com/blog/ssl-versus-tls-whats-the-difference.html
http://mihalos.gr/2013/04/03/ssltls-protocol-overview-part1/
http://www.codeproject.com/Articles/326574/An-Introduction-to-Mutual-SSL-Authentication